How to send a trojan horse services
A Trojan horse is a type of malware that is often disguised as a legitimate file or program. Trojans can be used to steal information, hijack your computer, or even delete files. In this article, we'll show you how to send a Trojan horse to another computer using a service like Gmail.
A Trojan horse is a malicious computer program that is disguised as a legitimate application. Trojans can be used to perform a variety of malicious tasks, such as stealing sensitive data, installing malware, or taking control of a victim's machine. Many Trojans are spread via email attachments or downloads from untrustworthy websites. To send a Trojan horse, the attacker would first create the malicious program and then disguise it as a legitimate application. The Trojan would then be sent to the victim via email or another method, such as social engineering. When the victim opens the Trojan, the malicious code would be executed, allowing the attacker to take control of the machine or perform other malicious actions.
To conclude, sending a Trojan Horse Services is not as difficult as it may seem. With the right tools and a little bit of knowledge, anyone can do it. Just remember to be careful and use caution when handling these tools.
Top services about How to send a trojan horse

I will send you a video of me wearing a horse mask making horse puns
Great gift for someone who enjoys puns, or someone you hate enough to make them sit through puns about horses.
*I do not record custom puns at the moment, only a customized ending*

I will record nearly anything you want as a horse race
Whether it's for your mates birthday/wedding, to help promote your business, a staff going away, phantom call of a real race...whatever! A horse race is a novel and exciting way to get your message across!
Just write a race for me to record and I'll send it back as a horse race!
If you want awesome sound effects (bugle, horses, race crowd etc), buy sound effects in the EXTRA's section.
OR for an extra $20 I'll write the race for you!..Just come up with the 'horse' names and 1 line of info on each 'horse' and I'll include it into the race! Tell me who wins, place etc or leave it to me! Up to 6 horses is $5, up to 10 horses is $10 and so on.
NB: The $5 gig IS AUDIO ONLY. Video extra.
Message me if you have any questions! Happy punting!
I will do equestrian,horse racing,equine logo

I will paint your text on horse stable gate
- Text color can't be changed.
- Capitalized text only.
- Maximum 18 characters.
- Don't provide your logo (text only).

I will remove trojan malware adware and risky infection etc
I am Microsoft Certified Professional.
- 100% GUARANTEE - Satisfied or its FREE!
- 100% MONEY BACK GUARANTEE
I have a 100% success rate and can remove Malware, Trojan , adware virus etc from Mac and all windows PC.

I will write your text on lake using lotus leaves with horse
Note:
1. Maximum 20 characters.
2. Don't forget to write the site name or text on placing the order.

I will sign a professional awesome horse racing logo your business
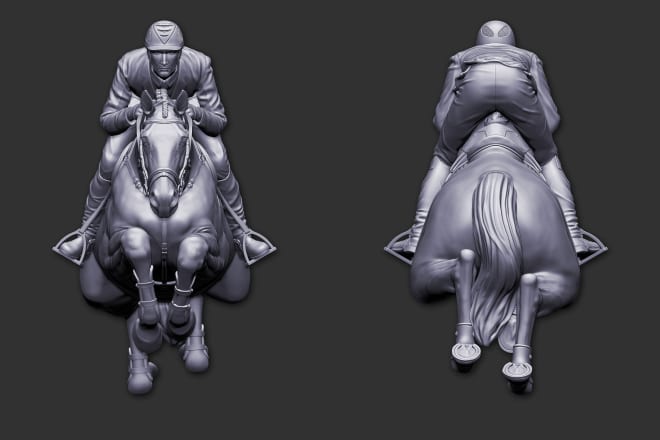
I will sell 3d model of a horse with jokey with commercial license

I will write your comedy script
