Linux ipsec centos services
Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged in a Linux distribution. Linux was originally developed for personal computers based on the Intel x86 architecture, but has since been ported to more computer hardware platforms than any other operating system. As of September 2015, over 70% of Internet-connected computers use Linux as their operating system, including web servers, mainframes, and embedded systems, such as mobile phones and tablets. The Linux operating system is widely used in many settings, from personal computers to supercomputers, from embedded systems to large-scale web servers. Linux is a leading server operating system, and runs the 10 fastest computers in the Top500 list. In June 2013, Linux was running on 3.13% of all computers, or, more specifically, on 5.82% of all Internet-connected computers. Linux also runs on embedded systems, which are devices whose operating system is typically built into the firmware and is highly tailored to the system. This includes mobile phones, routers, set-top boxes, media players, and more. As of November 2013, over 95% of the world's top 500 supercomputers use Linux, including all of the top 40.
Linux IPsec is a set of protocols used to secure communications at the network layer. IPsec is often used in conjunction with other protocols such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL) to provide end-to-end security. IPsec is a core component of many Linux distributions and is used by a variety of organizations to secure their networks. The CentOS project provides a free and open source distribution of Linux that includes IPsec in its default installation. IPsec can be used to secure communications between hosts, between routers, or between a host and a router. It can also be used to secure communications between a VPN client and server. IPsec uses a variety of protocols to authenticate and encrypt communications. These protocols include Internet Key Exchange (IKE), Authentication Header (AH), and Encapsulating Security Payload (ESP). IKE is used to negotiate a secure connection between two hosts. AH provides authentication and integrity for communications. ESP provides confidentiality and integrity for communications. IPsec can be configured to use pre-shared keys, public key cryptography, or a combination of both. Pre-shared keys are easier to setup but are less secure than public key cryptography. IPsec is typically configured using the strongSwan suite of tools. strongSwan is a free and open source IPsec implementation for Linux.
If you're looking for a secure, stable and reliable IPsec VPN server, then Linux and CentOS are a great choice. With a wide range of options and features, you can find the perfect solution for your needs. Whether you're looking for a simple point-to-point setup or a more complex multi-point network, Linux and CentOS have the flexibility and power to make it happen.
Top services about Linux ipsec centos

I will provide any type of support on microsoft, linux, vmware

I will solve issues of win or lnx,vsphere,aws, mikrotik,splunk
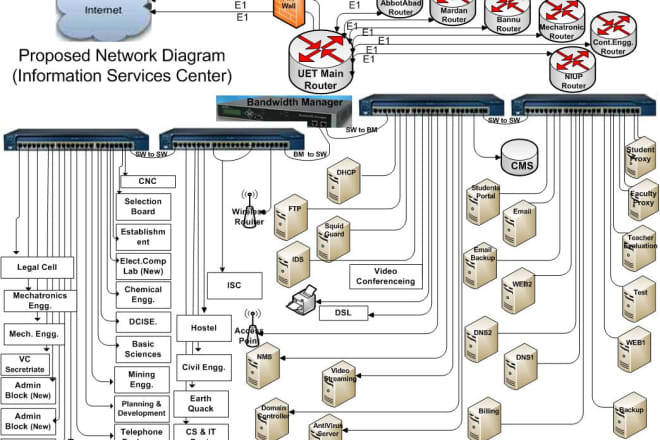
I will networking enthusiast and professional engineer
I will provide microsoft, linux, vmware, hyper v, virtual solution and support

I will do everything that linux or windows system administrator do

I will fix everything that linux or windows system
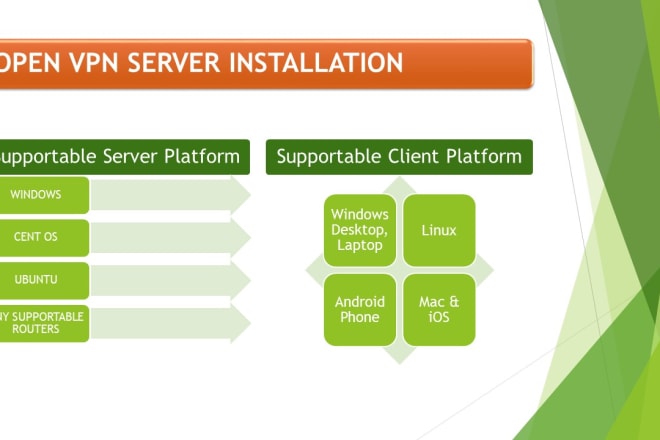
I will openvpn configuration on windows, centos and ubuntu
I will configure openvpn, anyconnect, ipsec, pptp, VPN on your linux
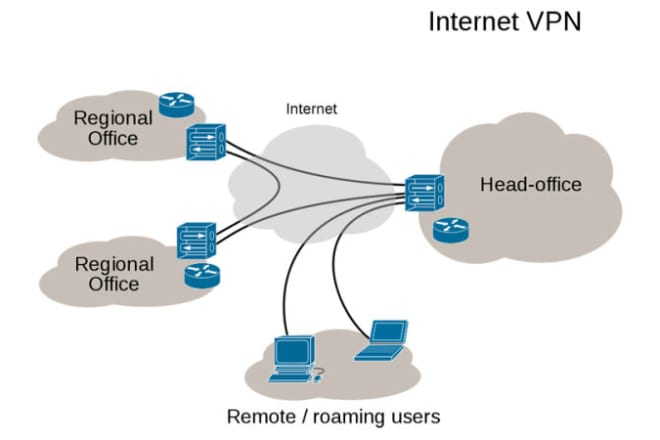
I will configure ipsec over gre,ikev2,pptp etc
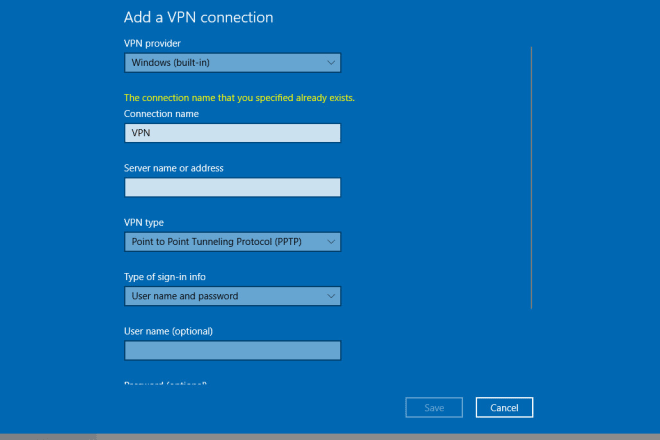
I will setup pptp,l2tp,ipsec VPN in your linux server
I will fix linux daiben ubuntu centos zabbix nagios cacti icinga2 pfsance kerio webmail

I will teach you to become a linux power user
I will teach you how to install any distribution of Linux like Debian, Fedora, CentOS, Ubuntu, Mint, Nimblex, Slackware, Deepin, etc I can help you with Linux related other problems too. The gig extras also includes teaching installation and configuration management that can lead to you becoming a power user.
This gig offers the following services:
- Learn basic Linux Concepts (1 gig)
- Learn over 20 basic Linux Commands (1 gig)
- Custom Linux Training as needed

I will provide support on linux environment
What I am able to do:
1) installing linux servers or desktop editions.
2) I have Most of the experience in centos, ubuntu, centos, mikrotik.
3) Network issues
4) Installing and configuring radius servers, sql servers, apache, tomcat, mediabrowser, plex.
5) Installing and configuring Crypto currency mining rigs. small and large scale.
6) PC/IT support.
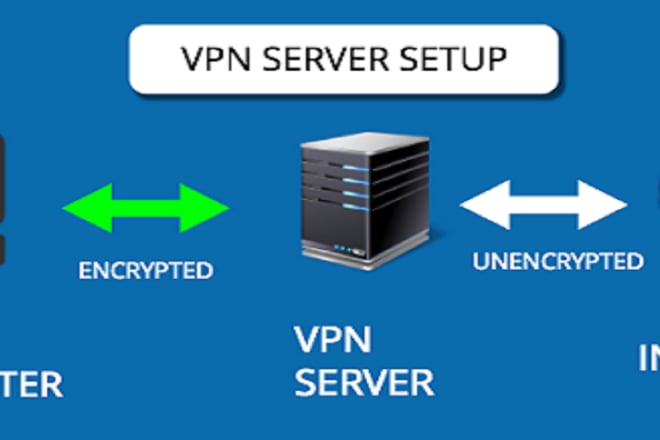
I will install openvpn, openconnect, ipsec, pptp VPN on linux
