Pen test online services
In recent years, the number of online services has increased dramatically. Many of these services are critical to the operation of businesses and organizations. As a result, the security of these services has become a high priority. One way to assess the security of an online service is to perform a penetration test. In a penetration test, a security researcher attempts to gain unauthorized access to the system. This can be done by exploiting vulnerabilities in the system, or by using social engineering techniques to trick users into giving up their credentials. Penetration tests can be very valuable in identifying weaknesses in a system. However, they can also be disruptive if not properly planned and executed. This article provides an overview of the process of penetration testing online services, and discusses some of the challenges that security researchers face.
A penetration test, or pen test, is an attempt to assess the security of an IT infrastructure by safely trying to exploit vulnerabilities. These vulnerabilities may exist in operating systems, services and application flaws, improper configurations or risky end-user behavior. Such assessments are also useful in validating the efficacy of defensive mechanisms, as well as, end-user adherence to security policies.
As more and more businesses move their services online, it's becoming increasingly important to test these services for vulnerabilities. A pen test, or penetration test, is a great way to do this. By hiring a company to test your online services, you can ensure that your customers' data is safe and secure.
Top services about Pen test online
I will jquery HTML ccs3 frontend development

I will do any kind of web design related work

I will design high quality responsive landing page

I will build a PHP website for you

I will design responsive landing page or full wordpress website

I will build,update and fix html, css, jquery php websites for you
I will test your app on all platform
I will write test cases for software QA
I will create macros to download test cases from hp qc
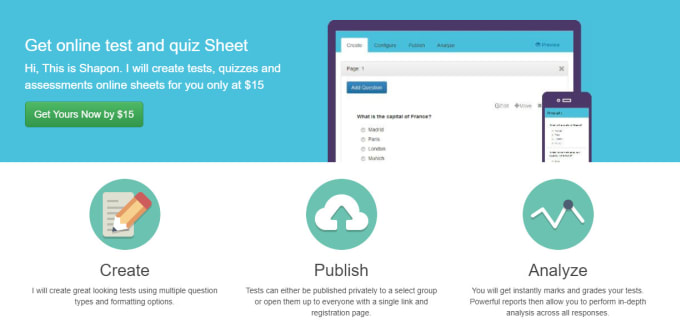
I will create online test and quiz sheet
I will create online test or survey using multiple question types and formatting options.
Are you looking for test sheets that could be used online and get the results to evaluates your students, new candidates, staff?
I can give you a solution.
Feature you'll get:
- Being online allows you and your respondents to access, administer and take your quizzes from anywhere at any time.
- Multiple questions, fill in the gap, drop down, file upload, random question, countdown, auto-grading
- User answers are stored in the database
- User is shown recommendation/result on the basis of their answers
- Automatically mark and grade your assessments, saving you the time to concentrate on what's important.
- The test can either be published publicly, privately or in a group.
- Print reports in pdf format
- Timed Test- Set limit of your tests
- Registration: User should be registered first
- Auto grading
- No question limitation
Send me a message before place the order for discussion

I will provide an actionable seo audit report for you website
I will develop test plan, detail test case and user stories
I will write your test cases and scenarios in software quality assurance
I will write your manual test cases and document test plan in sqa

I will do advanced penetration testing of a website or web app with professional report
